Understanding the cybersecurity mesh and its impact on your
5 (334) · $ 12.00 · In stock
Cybersecurity mesh sees the traditional security approach pivot away from the ‘walled city’ approach and evolve into a modular approach that views network assets as nodes with their own individual perimeters.

What is Cybersecurity Mesh? Principles & Architecture
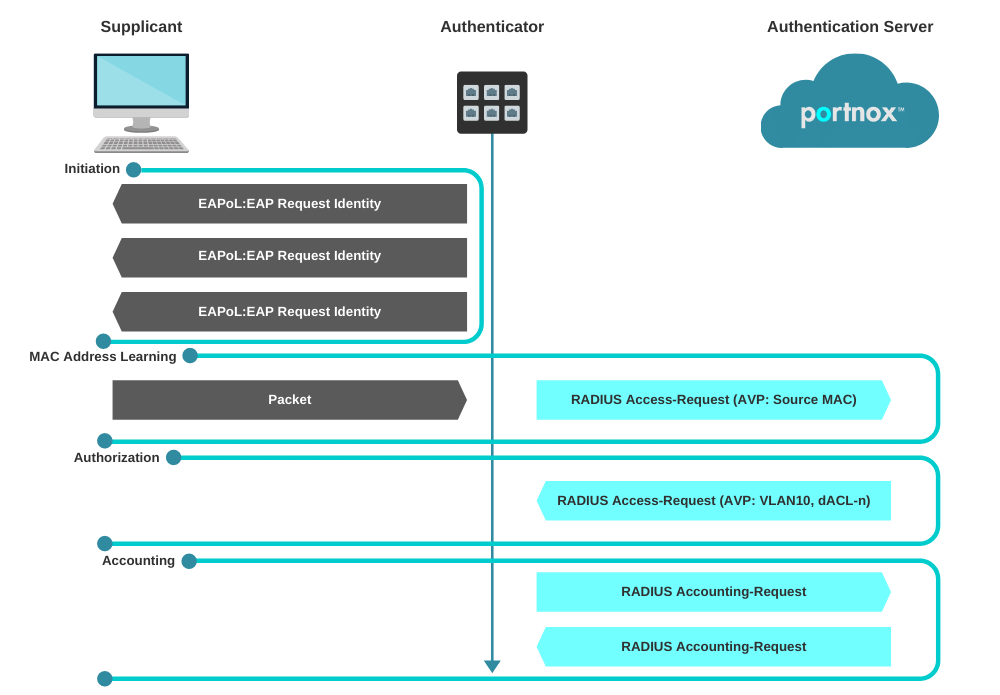
Monitoring 802.1X EAP: What You Need to Know - DataGroupIT

Data Security Archives - DataGroupIT

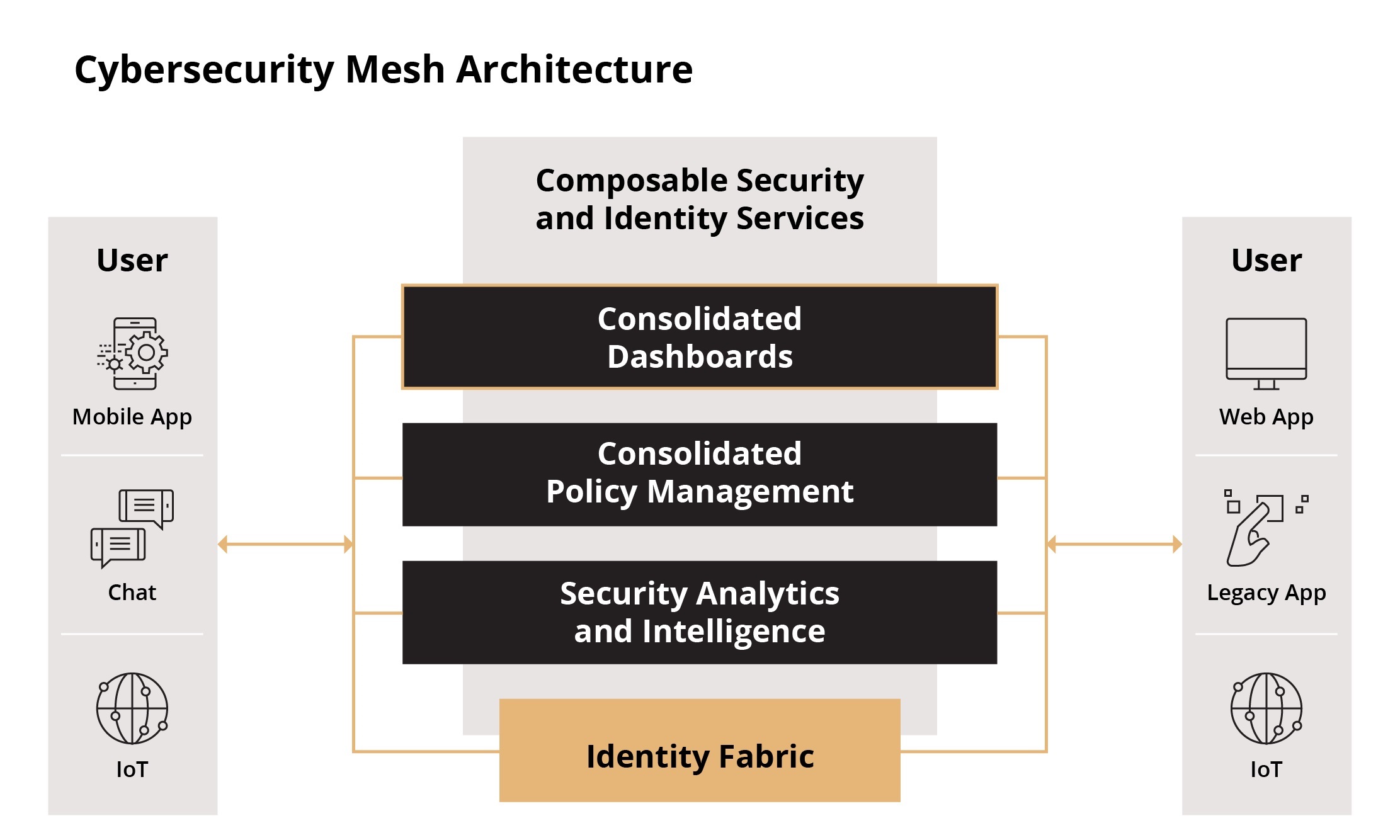
Cybersecurity Mesh Architecture is the Future of Cyber Defence

Cybersecurity Analytics: Definition, Solution, and Use Cases
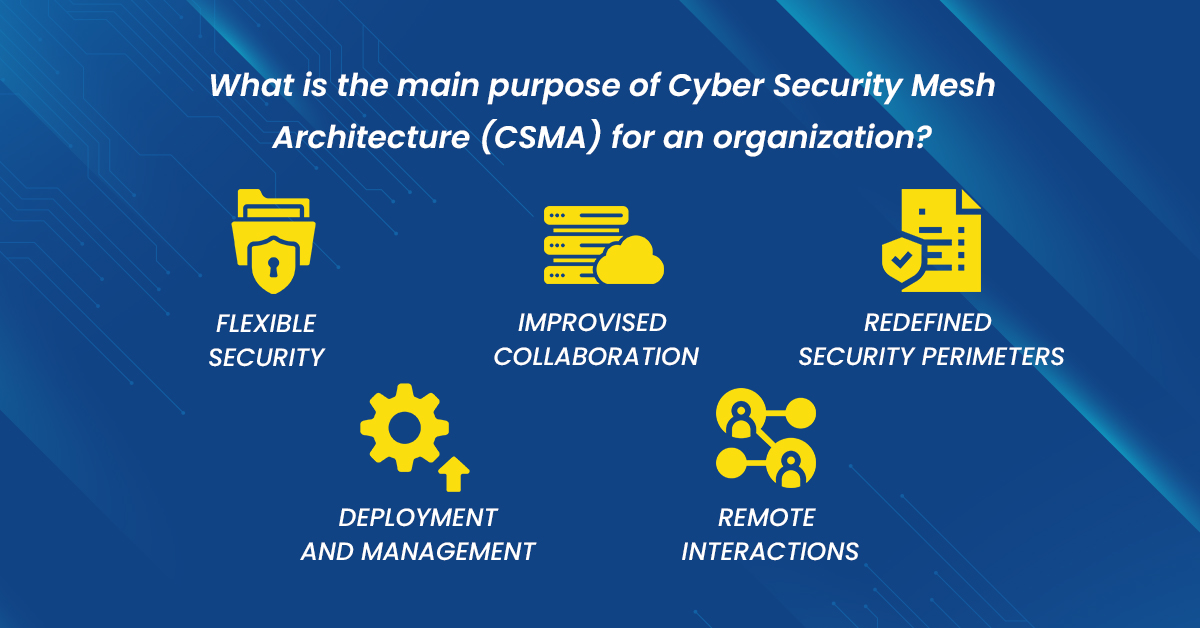
Cybersecurity Mesh – How does it impact your business?
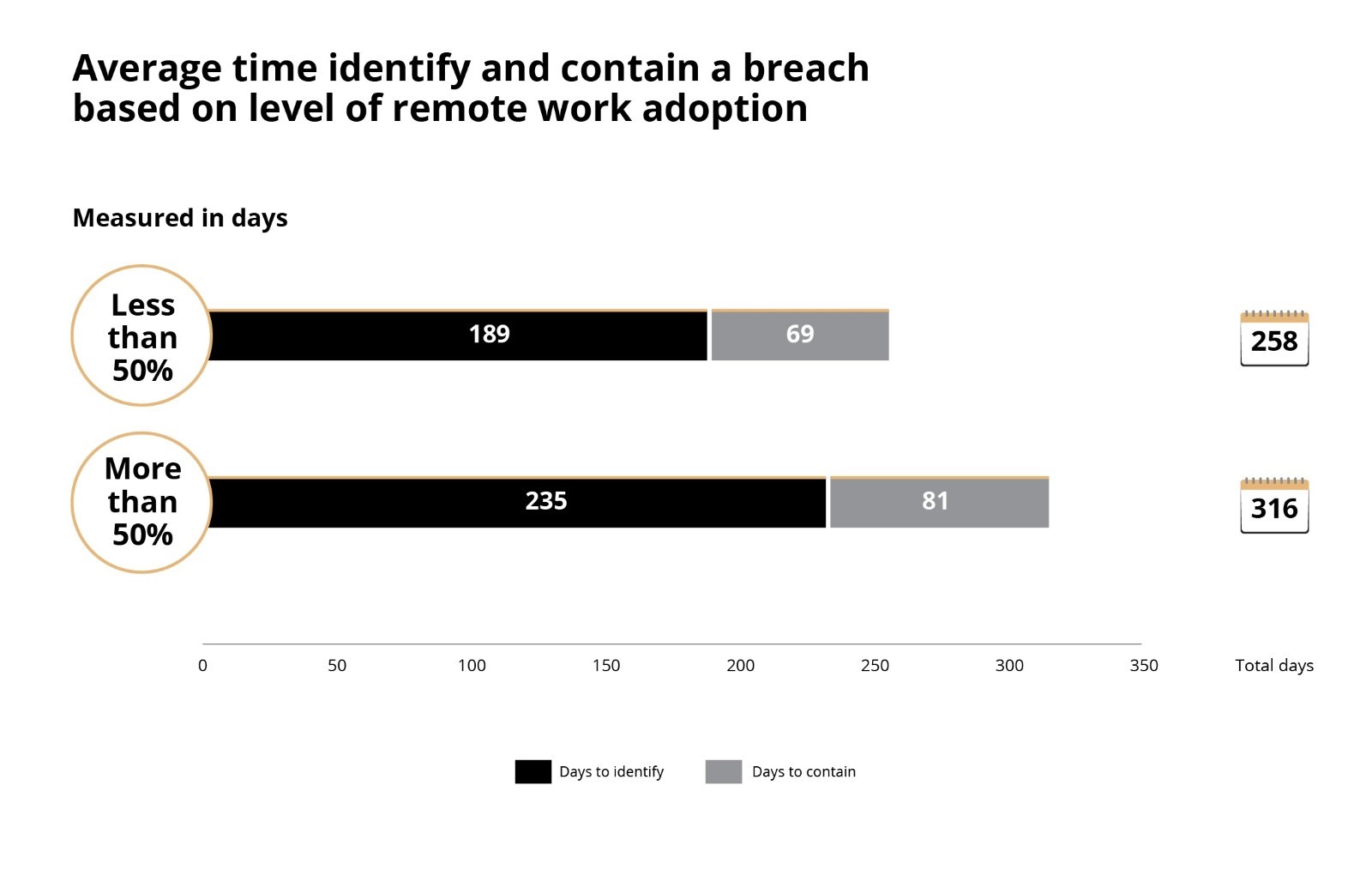
Challenges and Benefits of Cybersecurity Mesh
Challenges and Benefits of Cybersecurity Mesh

4 Key Reasons Why Your Business Needs Cybersecurity Mesh

Cybersecurity Mesh Architecture (CSMA)
What is a service mesh - Benefits and how they work - Cisco

What is Cybersecurity Mesh? Architecture, Definition, Tools