Dark endpoints: an invisible threat to your IT team
4.5 (159) · $ 5.99 · In stock

Invisible devices create significant blind spots that can leave IT departments helpless to act against a breach until it is already too late. A new report from Absolute found 13% of enterprise devices aren't connected to the corporate domain.
The Absolute platform delivers self-healing endpoint security and always-connected IT asset management to protect devices, data, applications and users — on and off the network.

To protect against ransomware, secure your entire web attack

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 29 July 2022

15 Hot Tools To Come Out of Black Hat and Def Con

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Briefing 01 July 2022

Forescout Technologies Inc.
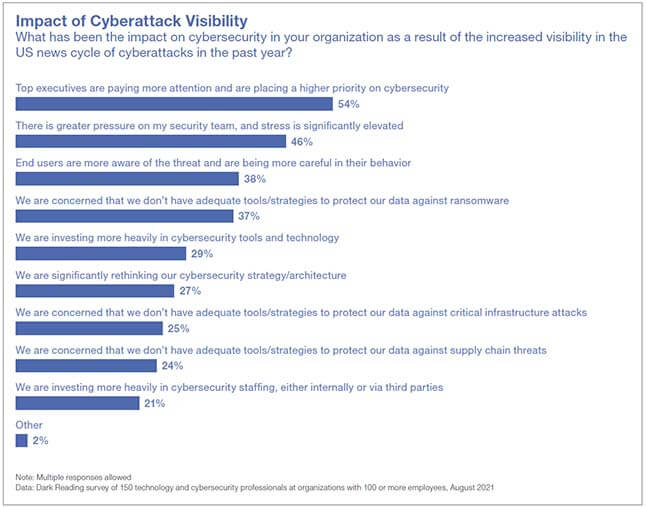
High-Profile Breaches Are Shifting Enterprise Security Strategy

Is the Dark Web Dangerous? What you need to know
Understanding Privilege Escalation and 5 Common Attack Techniques

Unmasking the Invisible Threat: Your Guide to Network Security






/chantelle-biustonosz-bezszwowy-absolute-invisible-c29260-czarny.jpg)
